Introduction
This guide walks you through the set-up and installation of connecting a Microsoft Windows box to a Linux (and UNIX as well) using putty generated SSH keys.
- Difficulty: Easy
- Time: 15 minutes
Requirements:
- Windows machine with admin rights
- Linux machine with user-level access (don’t need sudo)
- Internet connection (for downloads)
Install and Generating Keys
1. Download putty client for windows. Navigate to putty.org to get the download. That will have a URL (or list of URLs) that you can then navigate to to get the download (the download isn’t on putty.org natively).
2. I clicked through the link on putty.org to: https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html It looks like this site is the keeper of the Putty flame (at least at time of writing). Navigate there.
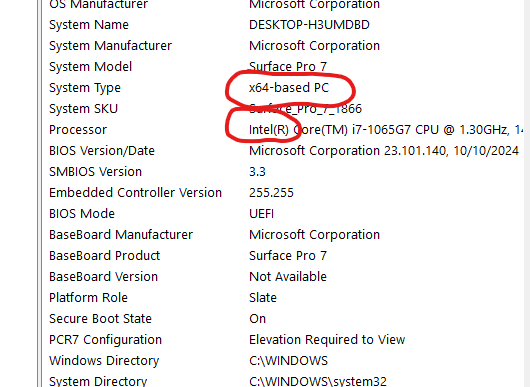
3. From there, I was given a table with download options. I looked to see what CPU architecture I needed on my Windows 11 box. I have a Microsoft Surface – some of them are ARM processors and some are x86. Typing “System Information” into the Windows search allowed me to select the System Information application (good icon for desktop BTW). From there I was able to see I had an 64-bit x86:
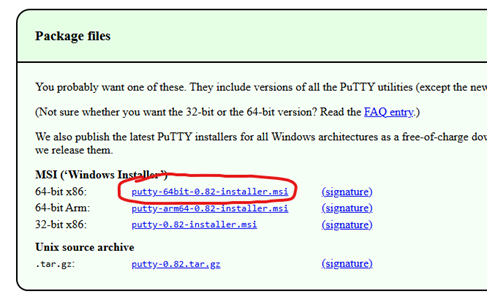
4. Thus, I chose to downloaded the 64-bit x86:
5. I installed it using the default location of “Program Files”.
6. I navigated to the install directory (again – Program Files). I then ran “puttygen.exe”.
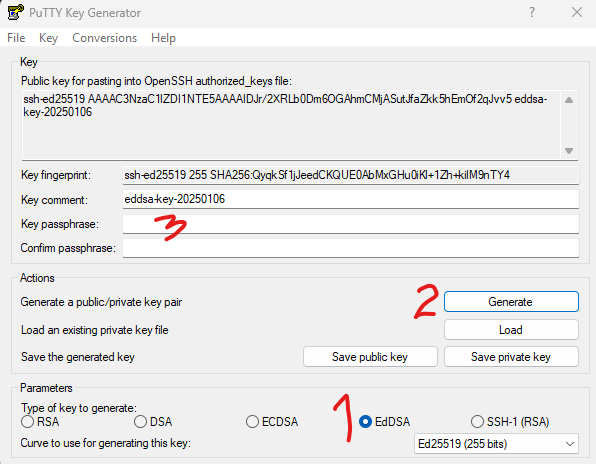
7. PuttyGen opened. Before I generated a key I did some quick research and decided that I wanted the newer EdDSA. I wanted something strong (encryption-wise) but well supported. Hopefully I chose well. I then clicked “Generate” and did the random noise thing with my mouse (you’ll be prompted to move your mouse around). I filled in the Key Passphrase boxes with a password to my liking.
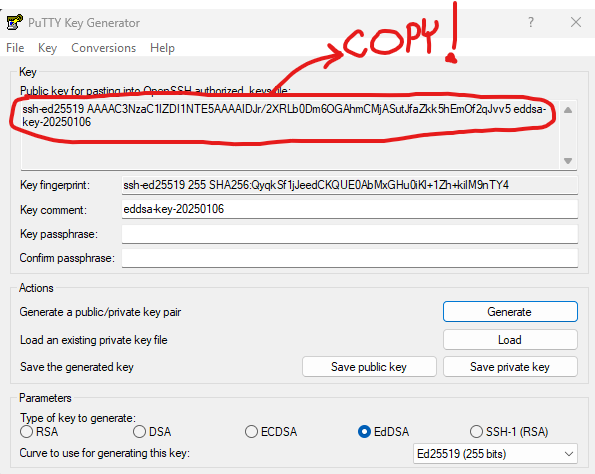
8. Now here’s the important bit… the bit that bites me every time. You need to save the text from the “Public key for pasting into OpenSSH authorized_keys file”!!! If you don’t, you will not have a file that will have a workable OpenSSH public key you can use. Go into notepad (or whatever plan text editor you use) and cut-and-paste the blurb into a file being sure not to add or remove any characters. Keep it safe! It’s your only link to put this key onto Linux/UNIX.
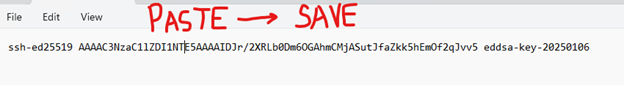
9. Save the public and private key using the Save buttons shown above. NOTE: THESE ARE NOT IN OPENSSH FORMAT AND WILL NOT WORK ON LINUX / UNIX! You’ll need the private key to connect to Linux boxes – so note the location of the saved files (esp. private key ending in .ppk).
10. Now get on the Linux machine and go to your home directory. “cd” into “.ssh” and do an “ls -la” to see if a file called “authorized_keys” already exists. If it does already exist, skip to the next step. If not, type “touch authorized_keys” and then “chmod 700 ./authorized keys” (all in the .ssh directory).
11. Okay – we’re still in the ~/.ssh directory here. Edit “authorized_keys” and add the line we copied above (the one you saved to a file after pasting it into notepad). The entry you add should be on its own line (not part of another entry, if one exists). Be sure not to add or remove any characters in the process.
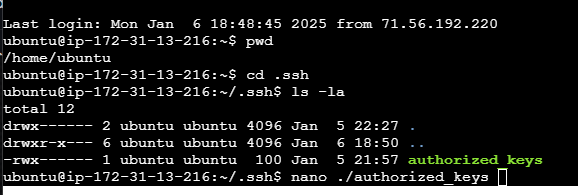
12. Save the file (CTRL-O, CTRL-X in nano; <esc>:wq in vi). Okay, the server side is all done!
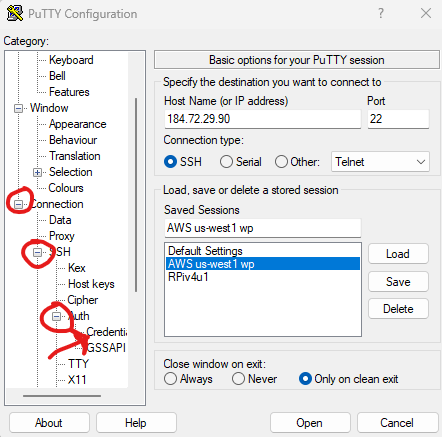
13. Open up putty (from the same directory as the puttygen) and put in an entry for the server’s IP address. Select SSH (selected by default).
14. In putty, open up “SSH section under “Connection” and go to the Auth -> Credential section. You’ll be at a new screen (shown below):
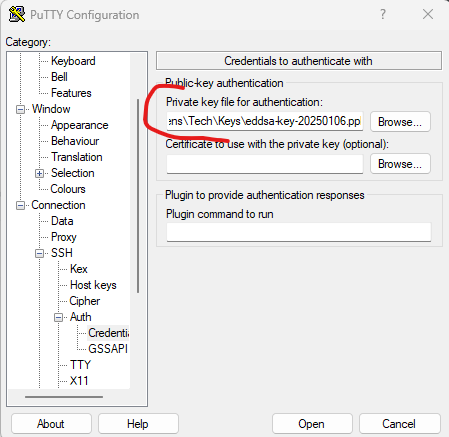
In the “Private key file for authentication” section go to “Browse” and select the file you saved above for the *private* key (should end in a .ppk extension if you let putty do this by default). You should know that this is your super-secret key (don’t give it out!) and that this key is specifically in Putty-format and will not work in OpenSSH (like much of the Linux world uses).
15. In Putty, go back to the “Session” in the left-hand pane. Double check the IP address of the server and Save the session.
16. Press “Open”. If all is right and good in the world, then you’ll get a pop-up asking if you want to allow the connection. You can press “Allow” or “Allow once” – up to you. If you didn’t check out the troubleshooting below.
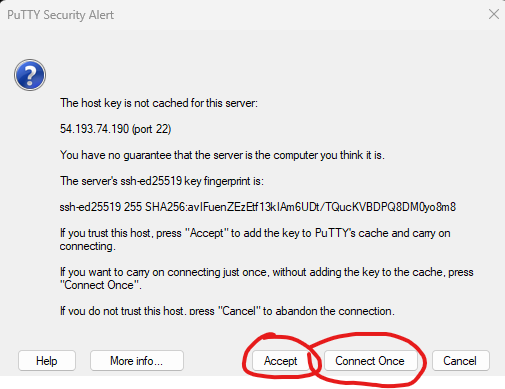
17. You might have to type a pass phrase if you created one with your key.
18. Done. Congrats!
Troubleshooting the Install
If you’re having trouble after following these steps try the following (in order):
* Make sure that your server has the SSH port open in the firewall (port 22). If you have telnet installed somewhere you can attempt to telnet to it on port 22 to see if it allows a TCP connection (but who has telnet nowadays). On the server, you can see if there’s a port listener up on port 22: “netstat -an |grep 22” or “ss -tulpn”.
* If you got a connected but got a key fail dialog then you might have pasted the public ssh key into the authorized_keys file wrong (double check). Make sure you didn’t add anything before or after the pasted line and that the link looks intact.
* If you are using a domain name rather than an IP address (to the server), make sure the DNS name is resolving using “nslookup <domain name>” at a command prompt. Make sure you’re getting an IP address back (and that address is what you expect the server IP to be).
* If that doesn’t work, I typically start by connecting from the server to the server itself (both client and server) using OpenSSH keys (ssh-keygen) but you’ll need to know how to do that, as it’s more involved troubleshooting.